This article explains all about MPLS VPNs and different VPN models based on MPLS technology. But before we start discussing MPLS VPNs, you should have an understanding of MPLS and its fundamentals that you can get from my article, Understanding MPLS Basics.
Understanding MPLS & MPLS VPNs
What is an MPLS VPN?
MPLS VPN is a virtual private network based on MPLS technology so as to transport different kinds of traffic using an MPLS backbone.
MPLS VPNs are one of the most popular use of MPLS in service provider networks across the globe. They enable a provider to connect geographically diverse customer sites over the MPLS backbone. MPLS VPNs can be categorised as follows:
- Pseudowires, Point-to-point MPLS VPN
- VPLS, MPLS based Layer 2 VPN
- IPVPN, MPLS based Layer 3 VPN
Let us have a look at each one of them in detail.
1. Pseudowires:
Pseudowiring is a technique for emulating a point-to-point connection over a packet-switched network. The Pseudowire is abbreviated as PW and acts as a transparent wire carrying a service. Common services that are carried over the wire include ATM, Frame-Relay, Ethernet while the packet-switched network may be L2TP, IP or MPLS.
This VPN service uses virtual leased lines (VLL) to provide layer 2 point-to-point connectivity between two sites to carry different L2 technologies and can even interconnect two different types of media such as Ethernet and Frame Relay.
When used for transporting frames over an MPLS network, the PW encapsulation is done using MPLS and the signalling mechanism is LDP. Cisco calls this AToM (Any Transport over MPLS) and this acts as a foundation for MPLS based L2 VPNs.
Pseudowires are also known as Martini Tunnels because they were developed by Luca Martini who delivered Frame-Relay service to end customers over MPLS. Later on, other services such as ATM, Ethernet, PPP and HDLC frames were successfully carried over MPLS as well.
PWs can be either be statically or dynamically provisioned. Static provisioning works for small networks, but becomes much more difficult and high-maintenance in large provider networks. Dynamic provisioning is implemented using OSPF-TE (open shortest path first – traffic engineering), ISIS-TE (intermediate system to intermediate system – traffic engineering), RSVP-TE (resource reservation protocol – traffic engineering) and LDP (label distribution protocol).
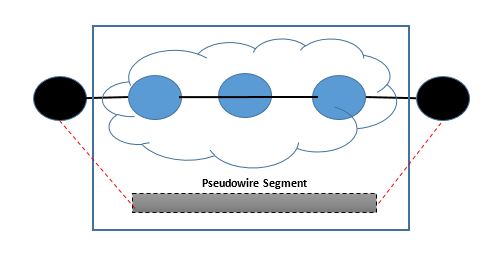
Today, pseudowire solutions are increasing rapidly in number and importance and have become a common method of transporting various services over MPLS cores. Pseudowires serve as a powerful tool for convergence that operators worldwide have built big IP core networks and are extending MPLS towards the edge of those network. PWs have many applications including Ethernet over IP/MPLS, SONET/SDH for Ethernet over MPLS, VPWS and VPLS.
2. MPLS Based L2 VPNs:
For an L2 MPLS VPN, the service provider is not bothered about routing and customer routes. The provider only renders a layer 2 pipe from one customer site to another over the MPLS core and customer needs to do routing configurations at his own end-devices.
So, the traffic from the CE gets forwarded to the PE router in Layer 2 format, carried by MPLS through an LSP (label switched path) over the provider network and then converted back to Layer 2 format at the receiving CE router.
Implementing a Layer 2 VPN on the router is similar to implementing a VPN using a Layer 2 technology such as ATM or Frame Relay. Layer 2 VPNs can be BGP based or LDP based and they are differentiated as follows:
BGP Based L2 VPN: The BGP based L2 VPNs are also called Kompella draft VPNs. In this type, the mechanism used by PE routers to communicate with each other about their connections is the BGP protocol.
The Kompella draft automatically setup new P2P links between new interfaces (possibly on new PEs) and this autodiscovery is based on BGP too.
LDP Based L2 VPN: This type is based on a draft that uses LDP to signal the VPN label between the PE devices. The LDP based draft is also called Martini draft VPN. The Martini requires explicit configuration of each P2P link and defines new TLVs/parameters for LDP to assist in the signalling of the VPNs.
Note that both these types, Kompella and Martini, create P2P L2 VPNs between logical interfaces and use same encapsulations.
It is also worth mentioning that there is a broad classification for L2 transport including VPWS (Virtual Private Wire Service) and VPLS (Virtual Private LAN Service). Let us have a brief look at each one them:
Virtual Private Wire Service (VPWS) – VPWS provides a virtual dedicated line between only two locations. Examples of VPWS services include Frame-Relay, ATM and Ethernet services over IP/MPLS.
It is also known as ETHoMPLS (Ethernet over MPLS) or VLL (Virtual Leased Line).
Virtual Private LAN Service (VPLS) – VPLS provides a virtual LAN between multiple locations. It is basically a way to provide Ethernet-based multi-point to multi-point communication over IP or MPLS networks.
VPLS is an end-to-end service wherein there are multiple instances sharing the same physical infrastructure. The word “private” tells that each instance of the service is isolated from the other. Hence, it allows geographically dispersed sites to share an Ethernet broadcast domain by connecting sites through pseudowires.
VPLS is designed for applications that require multipoint or broadcast access. One VPLS example is the Ethernet multipoint service.
Since VPLS emulates a LAN, full mesh connectivity is required. There are two ways for full mesh establishment for VPLS.
- Using BGP
- Using LDP
Note that VPLS is a two-label stack technology. The outer label is used for normal MPLS forwarding in the service provider’s network.
For the inner label, if BGP is used to establish the VPLS, it is allocated by a PE. On the contrary, if LDP is used, the inner label is a virtual circuit ID assigned by LDP using the targeted LDP session when it first established a mesh between the participating PEs. Every PE keeps track of assigned inner label and associates these with the VPLS instance.
Out of many of its benefits, VPLS is simpler and more cost effective to operate than a traditional service. Customers benefit because they can connect all of their sites to an Ethernet VPN that provides a secure, high speed network.
Furthermore, VPLS also provides an Ethernet space from a 10 Mbit/s shared LAN protocol to a multi-Gbps global service.
3. MPLS Based L3 VPNs:
MPLS L3 VPNs, also called IPVPNs, are the most frequently used MPLS VPN implementations in Service Providers.
The major difference between an MPLS based L3 VPN and MPLS based L2 VPN is that the service provider takes part in customer routing. The customer will run any IGP or static routing or BGP with the service provider and these routes then traverse over the MPLS core and are shared with other sites of the customer.
With Layer 3 MPLS VPNs, providers create VRFs on their PE routers. Customers connecting from different CE routers are then placed within a VRF on the same PE, after which they exchange routes with the PE using IGP, BGP or static routing.
VRF (Virtual Router and Forwarding):
Assuming that you have basic understanding of MPLS and its related terminologies, I am going to start discussing VRFs that allow multiple routing and forwarding tables to exist on a device. VRFs act as integral part in MPLS L3 VPNs because it makes a single PE router appear as different routers to CE devices. Customers having same subnets can be terminated on the same PE router as they end up reaching in different VRF tables.
In summary, VRFs make routing information from one customer completely separate from other customers and the routes are tunneled over the service provider MPLS network.
Note that “VRF” is a Cisco term and VRFs are called Routing Instances in Juniper and VPN Instances in Huawei. They are also known as Contexts by some other vendors.
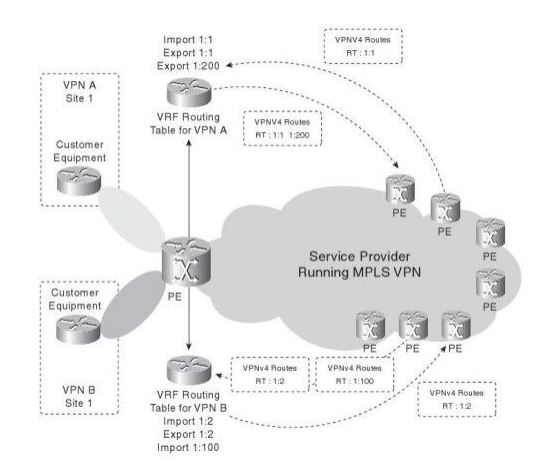
VRF Example Scenario: Let us take an instance wherein both customer A and customer B have got the same subnet, say 10.10.10.0/24 for their branch offices and terminate at the provider side on PE-01, they can be easily differentiated at the provider end on the basis of their respective VRFs.
However, it is important to note that VRFs are local to the router. So, we need to have an additional attribute that may distinguish the IP information in the MPLS core. So, this introduces the Route Distinguisher (RD) that differentiates a set of routes that are part of one VRF from another.
RD (Route Distinguisher):
An RD is a unique 64-bit number that gets appended to the conventional 32-bit IP address, thus making it a 96-bit VPNv4 address. The format used to represent RD is ASN:NN where ASN is the service provider’s AS number and NN is a number that identifies the site of the customer.
The function of RD is to make routes belonging to different VRFs unique in the MPLS core. To do this, we need to advertise VPNv4 routes and we accomplish this task using MP-BGP (Multi-protocol BGP).
RT (Route Target):
Now to get proper and correct routing across an MPLS VPN, we need to discuss Route Targets (RT). RTs define VPN membership as they allow the router to control the import and export of routes among different VRFs.
So, let us say if customer A located at branch X wants to have connectivity with customer A located at branch Y, the RTs will have to be imported and exported between respective VRFs.
MP-BGP (Multi-protocol BGP):
It is an extension of the BGP protocol that enables BGP to carry routing information for multiple network layers and address families. MP-BGP supports IPv4 unicast/multicast, IPv6 unicast/multicast and VPNv4 routes.
In order to exchange VPNv4 routes, MP-BGP uses NLRI (Network Layer Reachability Information) that comprises following attributes:
- RD (Route Distinguisher)
- IPv4 prefix
- Next Hop
- VPN Label
E2E Connectivity for L3 VPNs:
Now that you are familiar with technologies used in MPLS L3 VPNs, below steps would help you in understanding end-to-end flow for an L3 VPN:
- The CE connects to the PE using static or dynamic routing. Dynamic routing includes either an IGP or BGP. BGP is the preferred protocol as service providers already run BGP in their core.
- Once the CE-PE connectivity is established, the routes then enter customer’s VRF configured at the PE router. All customer routes learnt for this customer will be present in this VRF.
- The PE router will then redistribute everything into BGP. However, if we use BGP as a routing protocol between CE-PE routing, no redistribution will be required in that case.
- And last but not the least, in order to import and export routes, RTs serve the purpose.
It is important to note that service providers do also run LDP or any other tag distribution protocol over the IGP.
So, it works in layers starting from CEF or other vendor specific fast forwarding technique, MPLS, IGP, LDP, BGP and MP-BGP. Note that the routes floating in the MPLS core will be VPNv4 routes.
I’ll leave you with the following video “MPLS in a Nutshell” by Keith Barker in which he sums up the whole process of MPLS L3 VPNs in an easy but comprehensive manner.
In case you have any questions or feedback, please do comment below and I will surely get back to you as soon as possible.
Haider Khalid
Latest posts by Haider Khalid (see all)
- Getting Into Woodworking: Some Tips - July 9, 2025
- 5 Essential Tips for Maintaining Your Vehicle’s Performance - June 20, 2025
- 4 Steps To Manage Your Business More Effectively - June 14, 2025
Hi can you share your email or social id for some more information?
Hello Jim,
You can connect with me on LinkedIn mate – https://www.linkedin.com/in/haider-khalid/
all i can say to you is thank you for the wonderfull write up
Thanks, Michael. Glad that it helped 🙂
Could you give mail I’d or watsup
You can connect with me on LinkedIn at the following URL, thanks.
https://www.linkedin.com/in/haider-khalid/